Computer Viruses: Types and Prevention
Explore the world of computer viruses and their types with this comprehensive guide. Whether you’re a beginner or an experienced user, understanding computer viruses is essential for protecting your digital assets. Dive deep into the definition of computer viruses, different types, and how they impact your system. Learn about common viruses like malware, ransomware, spyware, and more, and discover proven strategies to combat them effectively.

- So What Is a Virus?
- The First Viruses (a Bit Of History)
- Types Of Computer Viruses
- Questions and answers
- Comments
So What Is a Virus?
A virus is a self-copying program. Many viruses do not do any destructive actions to your PC. Some of them can do little nasty things, like showing a picture on the screen, launching unnecessary services, opening adult Internet resources etc. But there are also viruses that can break down your computer by formatting the hard disk, rendering your data inaccessible or damaging BIOS in your motherboard.

How to Delete Any Viruses: Trojan, Rootkit, Ransomware, Spyware For Sure ☣️🛡️💻
First of all, we should discuss the most popular myths about viruses that you can meet on the web:
-
Antivirus is your protection from all viruses.
Unfortunately, that is wrong. Even having a very powerful antivirus with latest updates does not secure you from a virus attack. Nevertheless, you are more or less safe when encountering the viruses which are already known, the only threat coming from new ones that your antivirus database doesn’t know. -
Viruses are spread with any files.
It is false. For example, viruses are not spread with music, video or pictures, but they can often be disguised to look like one of such files, in order to make an inexperienced user commit a mistake and run a malicious program. -
If you got a virus on your computer, it is in big trouble.
It is also wrong. Most viruses don’t do anything but just infect other programs. Anyway, this fact is worth your attention – at least, scanning your computer with an antivirus having the latest update. If you have one virus, why do you think there cannot be more of them?! -
Not using email is the key to safety.
It won’t help you, I’m afraid. Sometimes you may receive emails from unknown addresses. It is better not to open these but delete them at once and empty your recycle bin. Usually a virus is in the email as an attachment by running which you get your PC infected. Keeping safe is quite easy – just don’t open emails from people you don’t know… Another good thing to do would be to adjust your anti-spam filters. -
If you copied an infected file – you got your computer infected.
In general, before you run an executable file, a virus will – just like any other file – just lay there on your hard disk and do no harm.
The First Viruses (a Bit Of History)
It all started in the 1960s -1970s in some U.S. laboratories. Their computers had, in addition to regular programs, some other ones that worked by themselves and were not controlled by anything. It would be nothing but they put extra load on PCs and wasted their resources.
In a decade, by the 1980s, there were already several hundreds of such programs. In 1984, the term “computer virus” was developed.
Such viruses would not hide from the user, but usually prevented him from working by showing various kinds of messages.
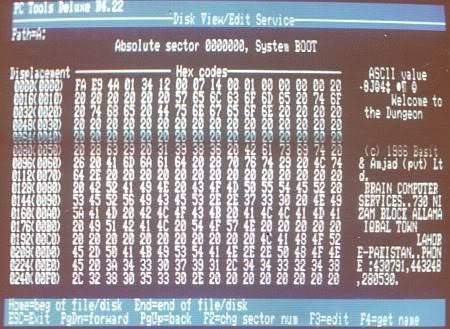
The year 1985 saw the emergence of the first dangerous and quickly spreading computer virus, Brain. However, it was created with a good intention of punishing the pirates who copied software illegally. The virus was triggered only on computers that had illegal software installed.
Successors of Brain existed for a decade when their number began to decrease sharply. Their algorithm was simple: they just recorded themselves into the file of a program, thus increasing its size. Antiviruses soon learned to determine if the size was wrong and find the infected files.
Types Of Computer Viruses

☣️ Did a Ransomware Virus Encrypt Your Files? Are You Looking For Ransomware Decryption Tools? 2021🚫
Type 1. Software Viruses
The viruses that could become attached into the body of a program were followed by other kinds that were separate programs themselves. The main problem was how to make a user run this malicious software? It turned out to be so easy! It should be named a “crack for so-and-so” and be posted on the web. Many will just download it and run it, in spite of their antivirus warnings (if they have one installed, of course)…
In 1998-1999 the world was shocked by appearance of the most dangerous virus, Win95.CIH, which damaged motherboard BIOS. Thousands of computers all over the globe were out of order.
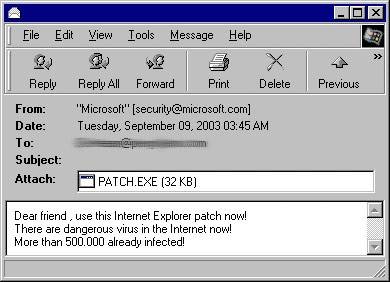
In 2003 a virus named SoBig was able to infect hundreds of thousands of computers because it was attaching itself to all emails that users sent.
The main method to fight such viruses is to update your Windows operating system and install an antivirus. You should also refuse to run any programs received from suspicious or doubtful sources.
Type 2. Macroviruses
Many users may not suspect that besides executable files like .exe or .com, there may be real threat in common Microsoft Word or Excel files. How is that possible? One day, these editors have been added VBA programming language to enable adding a macros as a supplement to documents. In the same way, if you replace the old macros with your own one, you can actually create a virus…
Nowadays almost all versions of office applications will ask you, before opening a document from an unknown source, if you really want to run a macros from this document, and if you click “Cancel” nothing will happen, even if there was a virus there. The paradox is that most users click “OK” voluntarily…
One of the most well-known macroviruses was Mellis which hit the network in 1999. , The virus infected documents and sent your friends emails with viruses inside with the help of Outlook client. Thus, dozens of thousands of computers all over the world were infected in a short time!

How To Remove Pendrive Shortcut Virus From Your USB Drive and PC 💥📁💻
Type 3. Script-based Viruses
Macroviruses as a separate type belong to the group of script-based viruses. The point is that Microsoft Office is not the only one to use scripts – other software packages contain them as well, such as Media Player and Internet Explorer.
Most such viruses are spread as attachments to emails. Often they are disguised as a latest piece of music or a popular picture. In any case, do not run and do not even open attachments sent to you from addresses which you don’t know.
Often users are misled by file extensions… It is common knowledge that pictures are safe so why can’t we open a picture sent to me in my browser?… By default, the file explorer doesn’t show file types. So if you see a file name like “interesting.jpg” it doesn’t mean that this is its true extension.
In order to see extensions, enable the following option.
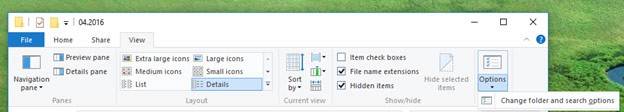
If you go to any folder, switch to View tab and select Options / Folder and search options you can get to View menu. This is where we find the necessary checkbox.
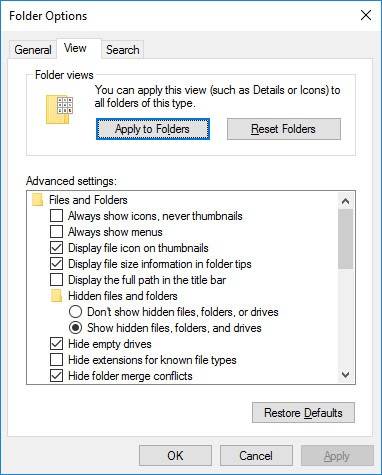
Uncheck the box for option Hide extensions for known file types and enable function Show hidden files, folders and drives.
Now if you look at the picture that you have received, it may appear that “interesnoe.jpg” has suddenly become “interesting.jpg.vbs.” This is the trick, in fact. Many beginner users have fallen for this trick, and many more will…
The main protection against script-based viruses consists in timely updating your OS and antivirus software. You should also say no to viewing suspicious emails, especially those containing unknown files… Regular backup of your data will be useful, too. The you will be protected against any threats for 99,99%.

How to Delete a File That Can’t Be Deleted Because of Write Protection or Denied Access 📁🔥🤔
Type 4. Trojan Software
Though this type was classified as a virus, it is not exactly one. Their infiltration to your PC is similar to that of a virus, but their tasks are different. If a virus strives to infect as many computers as possible and perform actions to delete, open windows,and so on, a Trojan usually has one task – to copy your passwords from different services or get certain information.
If often happens that a Trojan is managed remotely over a network and on the command from the owner it can reboot your PC or, what is worse, delete your files.
There is another peculiarity to be noted. While viruses often infect other executable files, Trojans don’t do it, because they are self-sufficient programs that run by themselves. Often they are disguised as a system process so that a beginner user finds it hard to tackle them.
In order not to fall prey to Trojans, firstly, do not download any files like “crack your Internet”, or “cracks” for some software etc. Secondly, you will need additional software to boost up your antivirus guard, such as The Cleaner, Trojan Remover, AntiViral Toolkit Pro and others. Thirdly, it would be useful to install a firewall (it is a program that controls Internet access of other applications) with manual settings where all suspicious and unknown processes will be blocked at your choice. If a Trojan cannot go online, you’re halfway to victory – at least, your passwords are not sent anywhere…
In conclusion, we would like to say that all measures and recommendations would be useless if the user, out of curiosity, runs unknown files, disables firewalls, and so on. The paradox is that viral infestation occurs through the fault of the user in 90% of the cases. In order not to become the victim of the remaining 10%, making a backup copy of your files would be a good thing to do. Then you will be almost 100% sure that everything will be all right!
If things went wrong with keeping viruses away from your computer and creating backup copies, you can try restoring your data with the help of one of data recovery programs.

How to Remove Adware Viruses /Ads & pop-ups From Any Browser | Remove pop up ads 🕷️🚫💻






Common symptoms of a computer virus infection include:
These symptoms can be detected by performing a full system scan with anti-virus software. Additionally, users should regularly check for any suspicious files or programs that have been installed without their knowledge.