Virus-Infected File Recovery: Exploring Your Options
Dealing with virus-infected files can be a nightmare, but is all hope lost for your data? In this article, we uncover the methods and techniques to recover virus-infected files. Our experts share valuable insights, tips, and solutions to help you retrieve those compromised files. Whether it’s malware, ransomware, or other cyber threats, we’ve got you covered.

- Dangerous Virus Effects
- How Viruses Infect Computer Devices and Delete Data
- Recovering Files Removed After a Virus Attack with Integrated Tools of the Windows operating system
- Recovering Files Encrypted by a Ransomware Attack.
- Recovering Files Lost After a Virus Attack with Third-Party Software
- When Malware Removal Becomes Urgent
- Conclusion
- Questions and answers
- Comments
Infecting a personal computer device with a virus can result in all kinds of adverse consequences, one of the most widespread effects being removal of user files. Our article will focus on restoring files after such virus attacks.
Dangerous Virus Effects

Most computer users have heard – and too many of them have experienced negative effects of malware, both in terms of possible file issues, and in terms of reducing the computer’s performance in general. Deliberately deleted or damaged user files, blocked access to certain elements of the operating system of the computer itself, selectively encrypted or modified files, erased or removed partition tables, getting your computer under control of outside hackers, involving it in remote illegal transactions or hacking other computers, personal data theft, spam sending and other nasty things are only a minor share of all those activities your computer may become involved in or subject to after it becomes infected by a virus.
Modern antivirus programs have learned to recognize and disable, isolate or eliminate malware and therefore protect computer devices from such risks. However, computer viruses are also evolving rapidly to implement varied algorithms and remote actions intended to enable their harmful effects. Too often, they succeed in removing user files completely or partially – and the situation becomes critical when such files exist in a single copy without any backups available.
Creating user file backups is a good element of your data protection strategy to withstand data loss that may come as a result of virus attacks. If you back up important files regularly, you can secure them against many types of data loss – caused by both malware effects and physical issues like a storage device suddenly breaking down.
However, the volume of data that we are using – and hoping to keep in safety – is growing constantly. It requires having several storage devices which means more extra expenses. It is no wonder then that many users prefer to keep all their backups on a single drive. As a result, getting it accidentally infected by a virus means losing or damaging both original copies and backups alike. That is why the question of restoring files lost after a virus attack becomes crucial for many users – especially when it appears as the first reaction after discovering such loss.
| Type of Virus | Description | Example of Impact |
|---|---|---|
| Trojan | Disguised as legitimate software, grants access to attackers. | Data theft, remote control of the PC. |
| Worm | Spreads independently over a network, infecting other devices. | System slowdown, network overload. |
| Ransomware | Encrypts files and demands ransom for decryption. | Blocks user access to data. |
| Spyware | Silently collects user data. | Theft of passwords and personal information. |
| Adware | Displays unwanted ads, redirects the browser. | System slowdown, appearance of ads. |
| Backdoor | Creates hidden access to the system. | Remote control of the device without user knowledge. |
| File Virus | Infects executable files. | Damage to files and applications. |
You can learn more about various malware effects by visiting our YouTube channel and watching this video: “A virus replaced files and folders with shortcuts in a USB drive: how to restore data and remove the virus”

How To Remove Pendrive Shortcut Virus From Your USB Drive and PC 💥📁💻
How Viruses Infect Computer Devices and Delete Data
A computer virus is a kind of autonomous and harmful executable code that can use certain vulnerabilities within the operating system to infiltrate into the code of other programs and system management files, reproduce itself and send such copies through various channels of communication to infect other computers. A virus or a medium for its propagation can appear in the form of either particular programs containing computer code or in the form of various data with attachments containing automatically executed commands that trigger the infestation process.

One of the main tasks for viruses is to spread themselves as widely as possible to achieve the goals of their developer (author). Most viruses are developed for one of the following reasons:
- As a joke without any negative or destructive effects indented.
- As a way to revenge an offence or unfair treatment.
- As a tool to enrich the author by stealing confidential data and selling it or withdrawing other people’s funds in an illegal way.
As viruses are developed for various purposes, so the extent of the damage they can cause to people’s computers also varies. Some viruses initially designed as a joke may show an pop-up picture, video or webpage that splash onto your screen unexpectedly and for a second only, which certainly creates some inconveniences for your work but cannot damage or remove your data. On the contrary, other viruses meant to inflict some damage are in fact designed to steal or remove important user files. Often such viruses cause problems in the work of hardware and software systems which then result in certain files or the entire operating system being deleted, disruptions in the structure of data allocation, preventing users from work by blocking their files completely or partially, increasing the number of system errors, starting resource-intensive processes and so on.
The main channels for spreading viruses and infecting computer devices are the Internet as the global informational network, local networks and removable media. Initially, most viruses were spread through the use of removable media when using a drive containing viruses could eventually infect many computers. Nowadays, though, the primary source of infestation is getting a virus from the network – for example, by clicking on a link received from unreliable or suspicious websites, an email etc. There is a number of threat-provoking actions that may potentially open the door to your operating system for a tricky virus:
- Using unknown software from doubtful sources.
- Connecting a storage medium (USB drive, memory card, external hard disk) to a personal computer or another device without checking it with an antivirus program.
- Visiting websites known to be involved in suspicious activities or containing viruses.
- Automatic or accidental downloading files from anonymous sources or questionable websites.
Actually, there are just too many ways for a virus to get inside your computer, and the harsh reality of life is that they are getting more numerous and sophisticated every day. That is why an important limiting factor to help prevent virus infestation is to always use trustworthy antivirus software especially when you have just bought a new computer or completed a scheduled reinstallation of your operating system.
In theory, viruses share a similar algorithm of action. Being attached to a kind of carrier – be it a drive or just a piece of data circulating throughout a network – the virus makes its way into a computer device and infects it. After successful infiltration, the virus may lie dormant until certain circumstances trigger its execution. This way, a virus remains invisible for a user and the computer shows no signs of virus infestation. When certain conditions are present, the virus begins its harmful activity by attacking system and user files, especially in computers within a certain network. As a result, its harmful activities damage the file system and operating system, change file names and even erase data which can be a terrible loss.
Summing up, it is evident that a computer virus can provoke major issues for proper operation of the computer and system services and result in loss of important data which may eventually lead to unwanted expenses. That is why recovering files deleted by a virus attack becomes a significant task that requires special attention.
Recovering Files Removed After a Virus Attack with Integrated Tools of the Windows operating system
This operating system features several built-in tools based on the backup approach which save user files in accordance with the user-defined settings. The Windows operating system cannot directly scan the computer for deleted or erased files and recover them. However, the functionality of its integrated tools makes it possible to back up a selective list of files and folders and restore them at your command if the original data is lost. The operating system offers several methods to try that give users good chances to detect and recover copies that can be used successfully instead of the lost files. An obligatory requirement for using these backup tools is to have them configured and enabled in the Windows operating system.
Method 1. Recovery from a Backup
If the Windows backup settings have been enabled previously, then you can restore date from such backup with the integrated system tools.
There are different ways to access the tool for data recovery from backup. For example, click on the Start button in the lower left corner of your desktop on the Taskbar, and open the main Windows menu. In the list of all installed applications, drag the slider down and find the section Windows System. Open the nested menu and select Control Panel from the list of available apps.

In the Control Panel window that opens, find and open the section Backup and Restore (Windows 7).
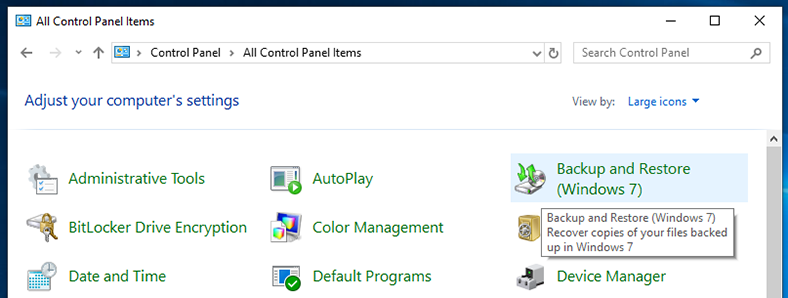
In the next window, scroll down to the Restore section and click on Restore my files.
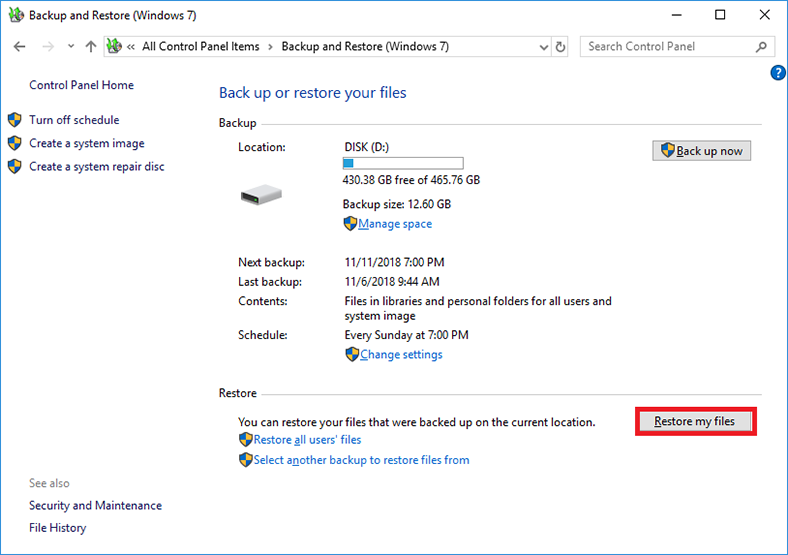
It will start a system-integrated file recovery tool working with a backup copy. In the new window, click on Search, Browse for files or Browse for folders and add the files you are going to recover from the corresponding archive.
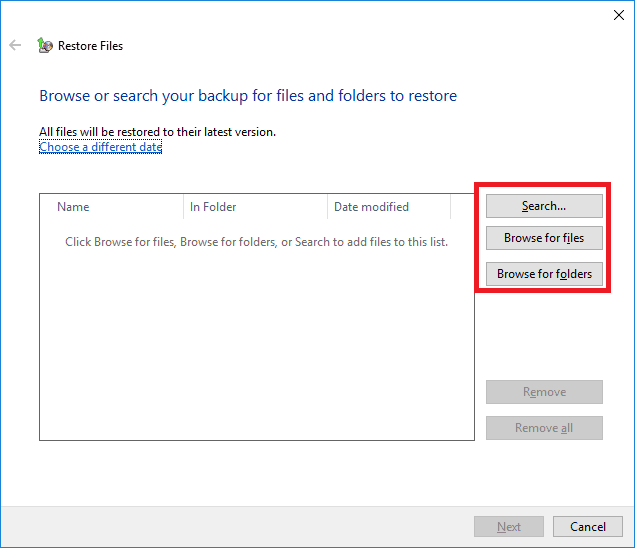
Then click Next to continue with the settings.
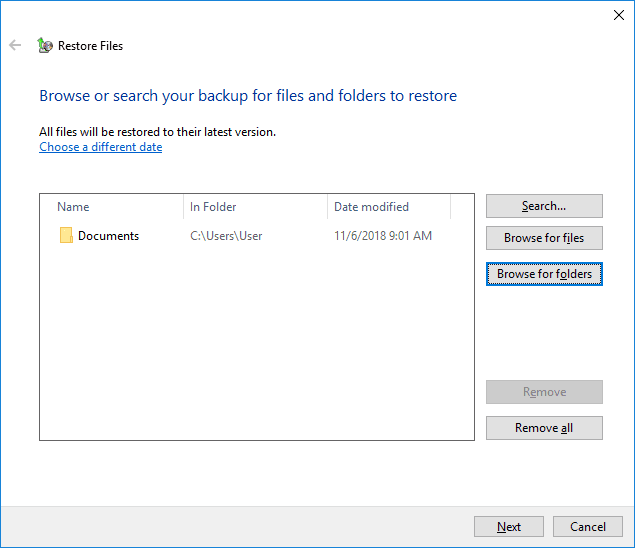
Choose a directory where to recover the selected files (a new location or the original one) and click Restore to accomplish the process.
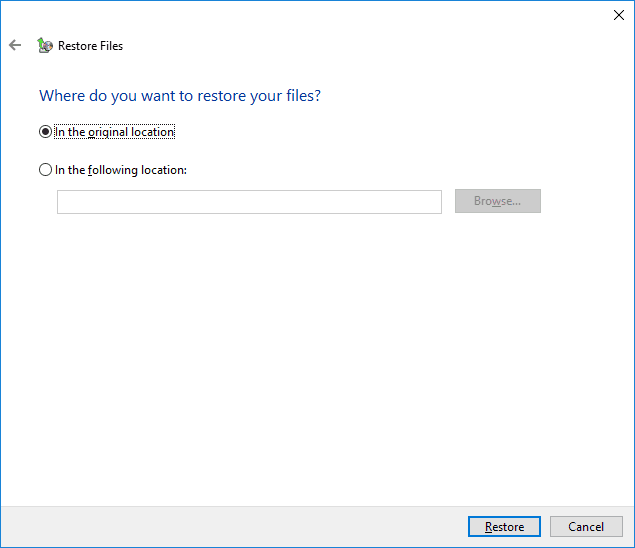
In the end, all selected files and folders will be restored according to the active settings.
Method 2. Recovery from Previous Versions
This method of file recovery is quite simple and can be used to restore a single file or folder as well as an entire logical disk. To start it, use Windows File Explorer. Open it in any way you prefer, for example, by clicking on the folder-shaped icon in the Taskbar.
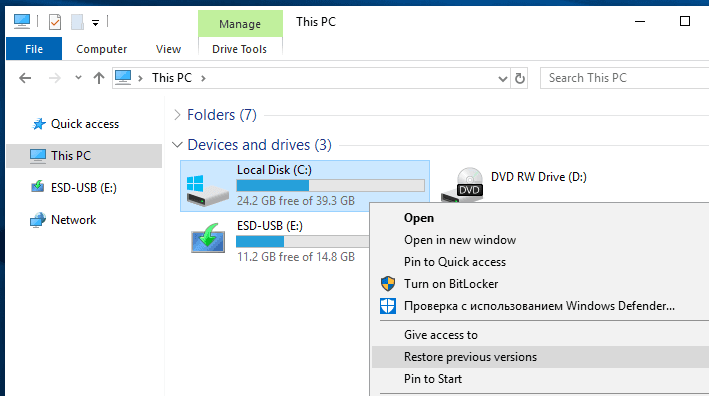
In the File Explorer window, select the necessary section, folder or file, and right-click on it. In the context menu, select Restore previous versions from the list of available actions.
In the Properties window, find the tab Previous Versions to see all previously saved files that the system created automatically based on the backup settings you have configured. Choose the necessary files and restore the data you were looking for.
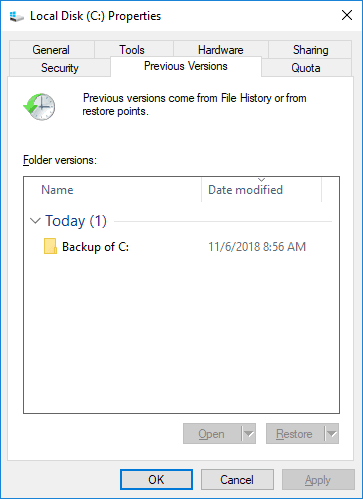
Bear in mind, though, that this method restores the previous version of your data and uses it to replace the current data. As this replacement operation cannot be canceled in any way, such recovery method should be used with caution.
Method 3. Recovery with File History
File History is a function to save previous versions of documents and other user files in the Windows operating system, and it enables recovering earlier versions of files after they have been modified accidentally, damaged, removed or affected by ransomware activities.
By default, File History in Windows regularly saves backups for all files from the folders selected by the user, and for the files from OneDrive cloud storage which are available locally on this computer, and keeps their older copies for an unlimited period of time. Users can restore various versions of files that can be viewed and recovered with the help of navigation buttons on the timeline.
You can open the File History tool in a number of ways: from the search panel, from the Settings or from the Control Panel. However, the easiest way to access File History of a certain folder or partition is from the Windows File Explorer. Open the File Explorer and go to the necessary folder. In the Home tab, find the Open column and click on the History button fashioned like a clock on the background of a folder.
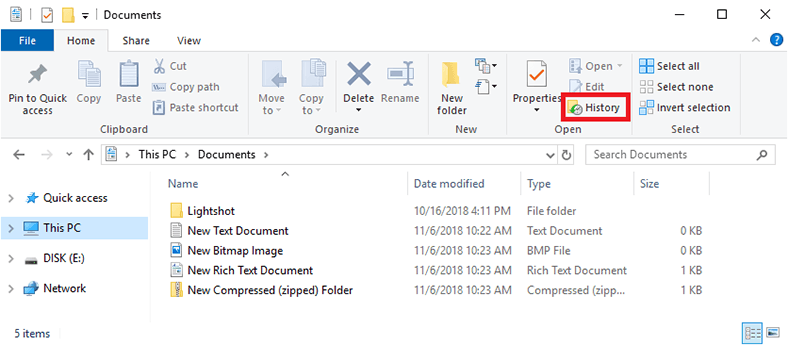
The File History window for this folder will open to show you numerous temporary copies of its files saved at different times and dates. Select the necessary copy of a file or choose all files and restore them by clicking on the round green button with a white arrow inside it – you can find this button between the other two buttons for switching between file versions.
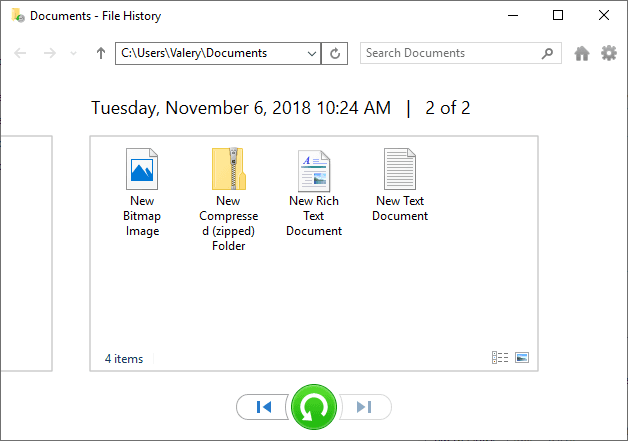
All selected files will be restored in a moment and available for use.
Recovering Files Encrypted by a Ransomware Attack.

A particular kind of Internet swindling that has become widespread recently is directly connected to encrypting user files by various malware and then demanding to pay a ransom for removing restrictions imposed on the use of the infected files and the operating system in general. This type of virus threats comes from malicious software classified as Ransomware.
Restrictions imposed on the operating system of a computer may vary by duration, have all kinds of additional requirements and is implemented in a number of ways.
Based on the system restrictions that can be visually perceived we may recognize two types of malicious influence:
- Blocking the operating system directly, with the ransom page shown on the screen, and the demand to pay a certain amount to unlock the computer.
- Encrypting most user data without damaging the system files to keep the OS running, with a demand to pay ransom for decrypting the files.
The common conditions of such swindling are as follows:
- Making PC users pay a ransom for unlocking their machines or decrypting their files;
- Malicious effects can be implemented in all kinds of devices (personal desktop computers, laptops, tablet PCs, smart watches, smart TVs and smartphones);
- Gadgets can be infected regardless of the operating system they have (Windows, Linux, OS X).
There are many types of ransomware and unfortunately, there is no single methodology for recovering user data that would work each and every time. All viruses belong to various families (classified by certain features), so if you can identify them, it’s a key to a successful attempt at restoring your files and unlocking your machine.
The general algorithm to eliminate a virus infection for all cases can be formulated as a series of steps:
- Removing the ransom demand or bypassing the screen lock;
- Restoring access to the operating system or decrypting the files damaged by the virus;
- Cleaning the system and removing the source of the virus invasion.
Some modern viruses may possess a combination of features that enable them to lock the computer and encrypt user data at the same time. That is why it is necessary to bypass the screen lock before you try restoring the encrypted files, and you can do it by starting the operating system in safe mode before you begin the recovery process. This way, you can prevent the virus from launching protective mechanisms which are intended to remove user data after a certain period of time.
Immediately after recovery, you should save the files to an external storage device and clean the operating system with an antivirus. In addition, it would be a good idea to format the disk that contained the virus. In some cases, you may have to reinstall the operating system as the viruses can damage certain system files or registry keys which prevents the OS from working properly.
The best protection against ransomware is to backup important user data regularly and quite often, and to prevent virus invasions of your devices by keeping your antivirus software and virus databases always up to date.
If the operating system is already infected, user data can be decrypted after malware effects with a special tool which tries to identify the virus family; if identification was successful, the tool provides the user with a special file that can decrypt the infected data.
On the Internet, you can use a free-of-charge web service where you can upload an infected and encrypted file or the file containing the demand to pay ransom and let the service identify the ransomware family; in some cases, this service can also help you decrypt the files if the virus family was identified.
One of such services currently containing information on over 600 ransomware products and updated regularly is ID Ransomware. When you upload an encrypted file or a file demanding to pay ransom, the service will compare certain patterns in the uploaded data against the ransomware database. If the ransomware family is identified successfully, the web service will give you a link to a step-by-step instruction on decrypting your files.
This is not the only service for such situation, and you can search specialized forums on the Internet for similar options. You can find more information on ransomware viruses, their peculiarities, and file recovery methods by watching this introductory video: “Are You Looking For Ransomware Decryption Tools? Has Petya. A encrypted your files? How to recover computer files encrypted by ransomware.”

Did a Ransomware Virus Encrypt Your Files? Are You Looking For Ransomware Decryption Tools? ☣️🚫📁
Recovering Files Lost After a Virus Attack with Third-Party Software
In spite of Windows operating systems having integrated tools for recovering user data, their functionality often turns out insufficient. The main reason is that the built-in mechanisms have several limitations and they are only useful in finding and restoring files under certain conditions (for example, backup and restore options should be enabled).

That is why users need an effective tool to help them restore lost data when important files were damaged ot removed by a virus attack. Such applications can be found among third-party data recovery software.
Despite the abundance of different software available globally on the Internet and varying in functionality, it is worth having a closer look at the well-reputed leader in data recovery – Hetman Partition Recovery by Hetman Software.
It was developed to recover data from hard drives, external disks, and any storage devices. The program combines a set of advanced algorithms which are capable of analyzing and searching for deleted information to enable its further recovery; also, they can restore data after system failures and various system errors, read information from damaged, inoperable, corrupt or inaccessible disks and provide access to lost or unreadable files. Hetman Partition Recovery supports all file systems used by Windows operating systems and is able to correct any errors in the logical structure of a hard disk to ensure safe recovery of the lost files.
A particular advantage is its ability to restore information damaged or locked by a virus attack. Due to having a perfect selection of innovative algorithms, the program is capable of recovering files after any kind of malicious influence meant to destroy user data or restrict access to it.
Download the installation file for Hetman Partition Recovery from the company’s official website and launch it. After configuring certain things, such as giving the installation path and deciding if you need a desktop shortcut, the step-by-step installation wizard will install the program to your computer quickly and successfully, so you are ready for action in a few minutes.
When the installation is complete, start the program. The program’s integrated tools will run a primary scan of the system and display all data storage devices connected to the computer.
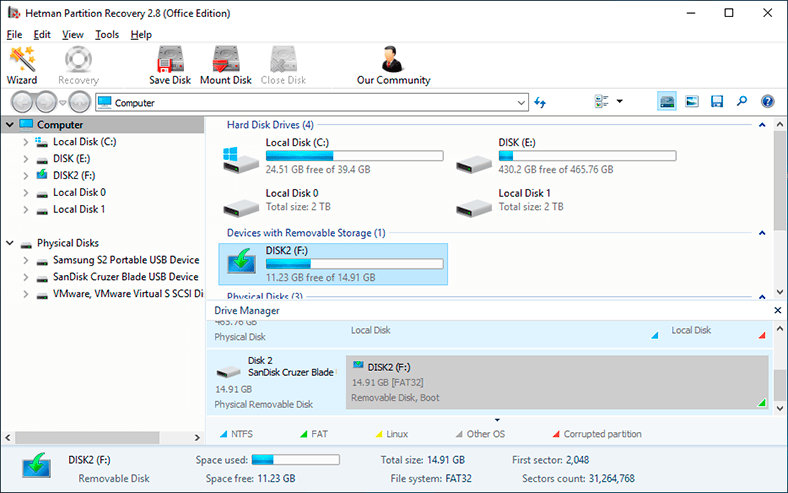
Select a hard disk partition or the entire physical disk by double-clicking on its icon in the program’s window. The program launches the file recovery wizard and it will suggest you to decide on the type of analysis you want to run now. If your files were lost after a virus attack, choose Full analysis to search and recover all available information from the selected disk by setting the point indicator next to the corresponding option Full analysis (searching for any available information). When you have chosen the analysis type, click Next to begin the recovery process.
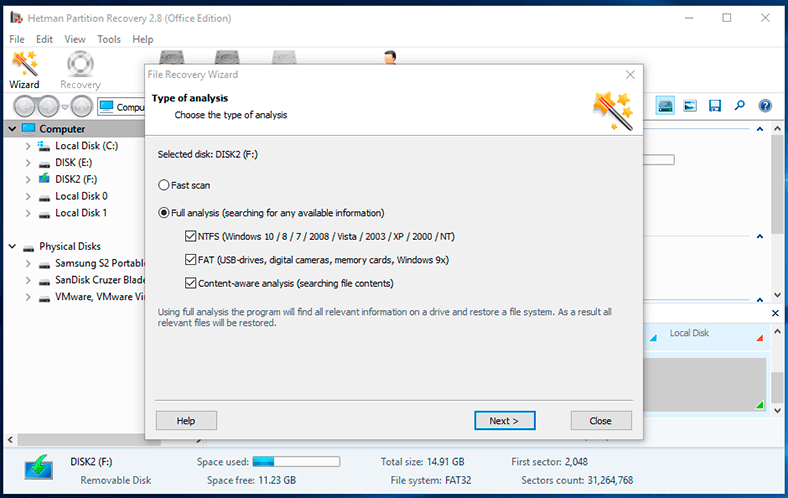
Depending on whether the files are more or less damaged, the size of the disk, its file system and a number of other additional settings, the recovery process may vary in duration from a few minutes to several hours. The line-type progress bar will show you the process of recovery in real time and in percentage, and will additionally show estimated time left until the operation is completed.
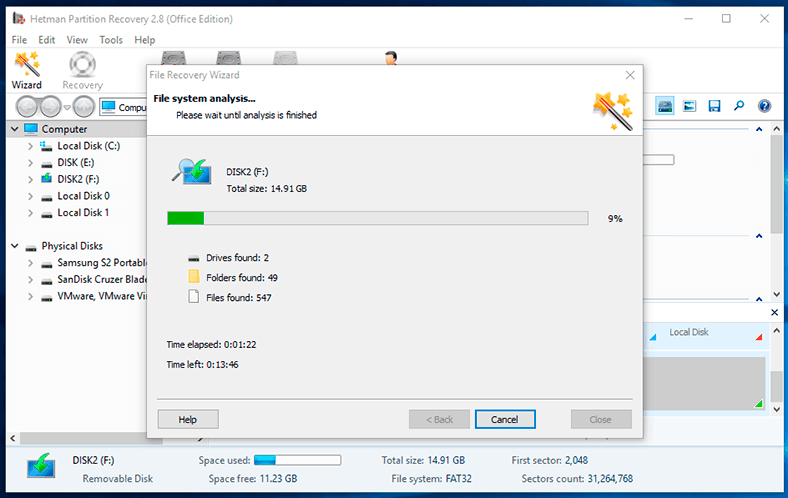
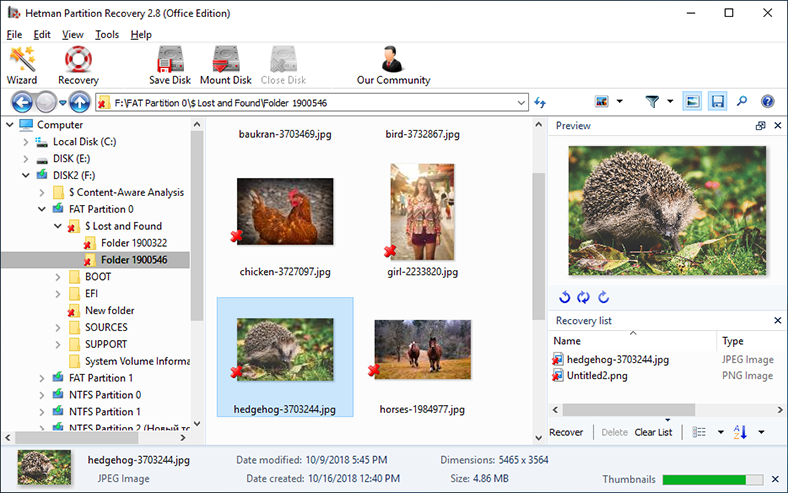
When the recovery process is over, the entire list of detected files and folders will be shown in the program’s window (which is made to look very similar to that of the Windows File Explorer for user convenience). By clicking on every file you can see their contents in the preview window. Having selected the necessary files and placed them onto the Recovery List by dragging and dropping, click on the Recovery button (fashioned like a life ring) which you can find in the main menu ribbon to save the selected data.
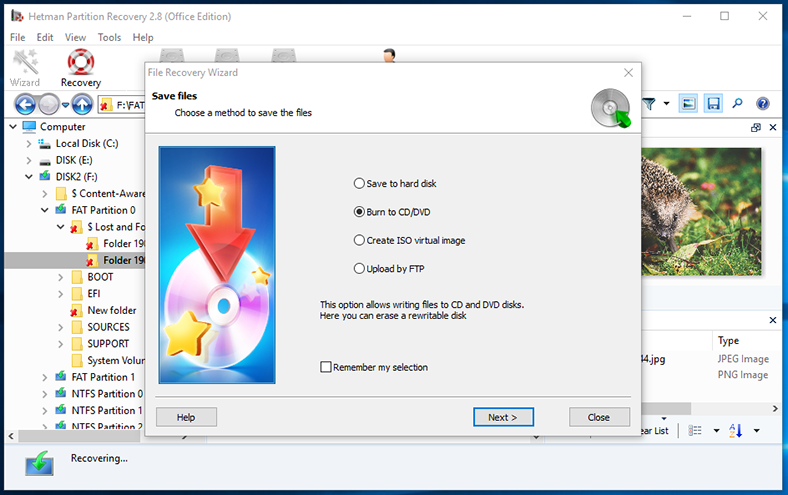
The Hetman Partition Recovery wizard will suggest choosing from the four possible ways of saving the selected elements: save them to a hard disk or any other stationary or removable medium, burn them to an optical disk, create an ISO image of the saved files or upload data by FTP protocol. Having chosen a few necessary options, for example, paths to save files, you can save your data according to the settings you have applied.
Now you can open the folder containing recovered files and check if they work properly.
When Malware Removal Becomes Urgent

Nowadays information technologies are developing rapidly, so almost every user is well aware of the virus danger, the importance of eliminating it at once and giving proper attention to system safety. However, there are tricky aspects to keep in mind when it comes to when the computer has to be cleaned from viruses.
When a computer is infected, the virus begins to reproduce itself and damage the user data and the operating system thus affecting its reliability. Hence the best solution is to keep viruses away from your machine and use a good antivirus offering powerful protection against malware infiltration.
However, if the computer is already infected, the natural desire to clean the operating system from viruses may have its negative consequences as well. When removing a virus, the antivirus program may also delete some useful files too just because of the algorithm it is using. As a result, you can get more files in your computer damaged or deleted, and some data can be lost forever. So it would be better to complete the data recovery process first, and only them move on to cleaning the disk from malware.
Conclusion
The widespread application of computer devices, their ease of use and impressive functionality ensure their leading position in the field of processing and storing data. Considering the high popularity of computer devices and the rapid development of the global information network, with most data transformed into digital formats, there are growing risks to become subjected to devastating effects of various malware designed to damage user data or steal their personal information for illegal purposes.
New viruses are released every day, their numbers are growing at the frightening rate, and they are causing enormous damage to users and their information. Using powerful and up-to-date antivirus tools reduces the risk of virus infection significantly, but due to the wide range of algorithms employed by viruses to search for system vulnerabilities, even this requirement cannot give you a 100% guaranteed protection for your precious data. As a result, user data can be damaged or lost for good.
Meanwhile, Windows operating systems have built-in backup and restore tools that can help you get the lost data back in most cases.
In some cases, though, protective elements inside Windows are not enough. That is why it is always important to have professional data recovery software such as Hetman Partition Recovery capable of restoring any type of user data lost after a virus attack or any other problems.
If you have questions about recovering files infected by a virus or if you have particular experience and would like to share it, leave your comments under the article and we will answer them without fail.