What to Do If Your Files Are Encrypted: Complete Guide
Learn what to do if your files are encrypted with this comprehensive guide. Whether you’re dealing with ransomware, malware, or accidental encryption, this tutorial covers everything you need to know. Dive deep into step-by-step instructions and essential tips for handling encrypted files and recovering your data. Don’t let encryption hold your files hostage!

- Overview of the Problem
- Actions To Take When All Necessary Data Is Infected
- Data On Your PC Encrypted In XTBL Format
- The Actions That We Do Not Recommend
- Data Infected By better_call_saul
- Trojan-Ransom.Win32.Aura и Trojan-Ransom.Win32.Rakhni
- Variants of The Encrypting Virus
- Protection From Encrypting Viruses or Ransomware
- Questions and answers
- Comments
Overview of the Problem
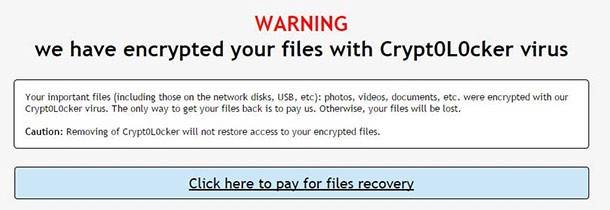
There are several versions of this virus, and new modifications come out all the time. However, all of them employ one principle. When they make it to a computer, they encrypt documents, pictures and other files that can be useful for the user (their formats are changed in the process) and delete original files. After that, a message appears on the screen saying that the files are encrypted, and you have to send some money onto the swindler’s account to get your files back to normal condition.

Did a Ransomware Virus Encrypt Your Files? Are You Looking For Ransomware Decryption Tools? ☣️🚫📁
Actions To Take When All Necessary Data Is Infected
To begin with, you should learn general information about people who also faced this problem. If the information on your computer is really infected, there is no reason to get upset yet.
If possible, take an infected file from the PC affected by the encrypting virus to another media along with the file containing the swindler’s demand t pay for decryption. After that, switch off the PC so that the malware cannot influence other files as well. All further work should be done on another computer.
Now it is time to find out what virus infected your data. For this purpose, you can use samples of encrypted files. In some cases, decryption devices can be applied. For other viruses, these have not been invented. However, this circumstance should not prevent you from sending samples of infected files to antivirus laboratories for examination.

How To Remove Pendrive Shortcut Virus From Your USB Drive and PC 💥📁💻
A search engine can help you to find out which one can be decrypted and which cannot. You can look for forums where this problem is discussed or find the encrypting virus type by searching for its format name. Besides, some services appeared on the Internet that help determine the encrypting virus type. Their effectiveness is still not clear but they are nevertheless worth trying – what if it helps?
If you managed to discover the type of the encrypting virus, then you should search the web for a utility that can decrypt it. Such programs are distributed by antivirus developers free of charge. Besides, never hesitate to contact an antivirus developer’s support service.
Yet it should be noted that such actions do not always help, and not every piece of decrypting software works correctly. In such situation, some people choose to pay the swindlers and thus encourage them to go further. Other users turn to data recovery software, because encrypting viruses delete original files – which can be recovered, theoretically.
Data On Your PC Encrypted In XTBL Format
This malware is one of the latest. It replaces your files by .xtbl format files and changes the names into an unreadable set of symbols. At the same time, a file readme.txt appears with the text that the user data is blocked and you need to send a code to a certain email address if you want your data unlocked. When you do that, they promise you will be sent instructions how to eliminate the problem. If you take any actions without these instructions, you can lose your data without chances to recover it.
Nowadays it is impossible to decrypt .xtbl format. Some users who stored very important information on their computers sent the swindlers quite big sums of money to receive a decryption utility, but things do not always end that way. Sometimes the money is sent, but no utility is received.
There are many recommendations on what to do if you find .xtbl encrypted files on your computer. In some topical forums, there is even advice to turn the computer off at once or to take no actions against the virus. However, these steps are excessive and can damage your PC. That is why should act differently.
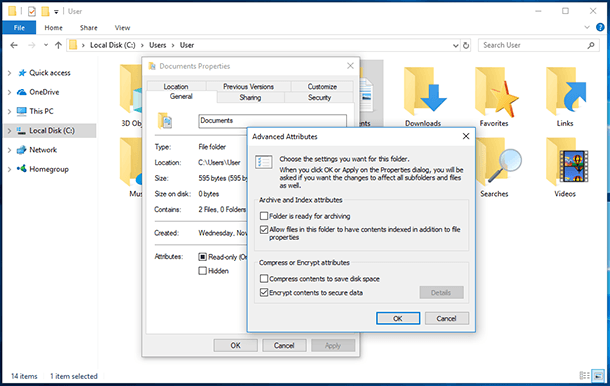
First of all, go to Task Manager and end tasks related to the encrypting procedure; make sure the computer is disconnected from the Internet. After that, write down the code that the swindlers want you to send by email. In this case you don’t need to record it on your PC in a text file because it can be encrypted by the virus.
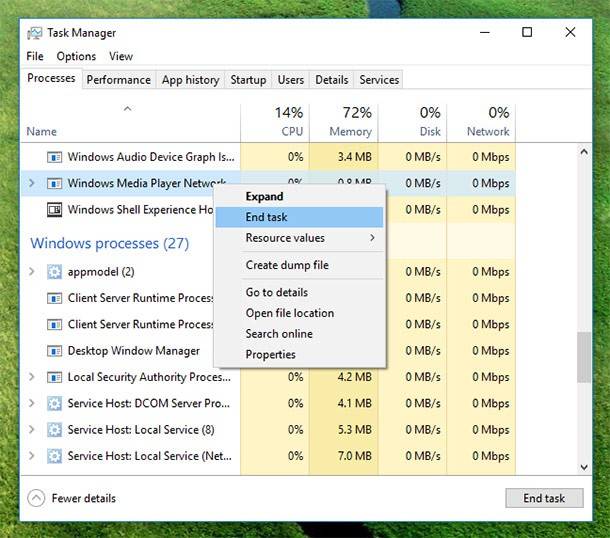
Your next step is to try deleting the encrypting virus with some specialized software. You can try several ones one by one, but if your PC has got an antivirus installed, your installation of another one may result in conflicts and incorrect work of the computer.
As you do it, wait for a decryption program to be published by leading antivirus developers. In addition, you can send an encrypted file and the code to an antivirus developer website. If you have an original version of the encrypted file, it is recommended to send it too. It may help the specialists decrypt the file quicker.
The Actions That We Do Not Recommend
In no case, do not rename such files, modify their extensions or liquidate them if the files are of any value to you. This is all we can recommend if your PC is infiltrated by a virus encrypting data into .xtbl format nowadays.
Data Infected By better_call_saul
One of the latest encrypting viruses to be mentioned is Better Call Saul. It transforms the encrypted data into .better_call_saul format. It is not known so far how to decrypt such files. The users who asked Kaspersky Lab for help were told that decryption is not possible yet. However, it is worth trying because the more samples of encrypted data a laboratory receives, the sooner it may solve the problem.
Trojan-Ransom.Win32.Aura и Trojan-Ransom.Win32.Rakhni
This Trojan virus also encrypts files and can give them several extensions. In order to decrypt data affected by this virus, you should go Kaspersky Lab website and download their free application RakhniDecryptor.
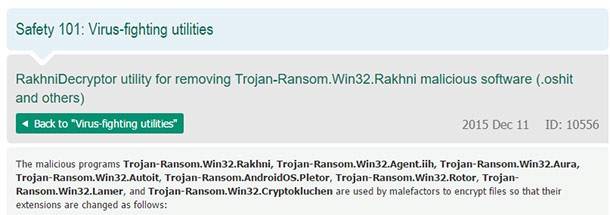
Also, on the same page you can find the manual for this software. There you can see how encrypted data is recovered. In this situation the only thing to do is to uncheck the box “Delete encrypted data after successful decryption.”
If you have a licensed copy of Dr.Web antivirus, you can use one of its applications for decryption. You can find it in the official technical support page of the company website.
Variants of The Encrypting Virus
Not so often, but sometimes there can be various Trojans that encrypt files and then demand money for their decryption. Below, we describe methods to eliminate them as well as links where you can download a decryption utility and learn the signs of suchlike pests living in your computer.
However, the best method to use in this case will be scanning your PC with an antivirus to find out the virus name in accordance with the antivirus developer’s database, and then look for a toll to solve your problem.
Protection From Encrypting Viruses or Ransomware

How to Delete Any Viruses: Trojan, Rootkit, Ransomware, Spyware For Sure ☣️🛡️💻
As the virus known as Ransomware is becoming more and more widespread these days, many antivirus developers began creating their own tools to combat this malware. Many of these are still in their testing phase and cannot fight any virus of the kind, but they are distributed free of charge.
Also, there are applications provided on a fee-paying basis, which can eliminate almost al types of ransomware, with additional protection for local and network drives.
However, these utilities cannot decrypt files – they can only stop the virus from encrypting them. Anyone would like to find such functions in antivirus software, but now a user has to keep a whole band of programs to feel protected: an antivirus, an antimalware utility, and now – a specialized utility to defend the PC against such as Anti-ransomware and Anti-exploit.
By now, that is basically all you need to know about file encryption. If you observe the recommendations above, you can avoid unfortunate consequences. You shouldn’t send money to the swindlers, because they may or may not provide you with a decryption utility. In any case, when you face this problem it is better to ask for help from advanced antivirus developers.
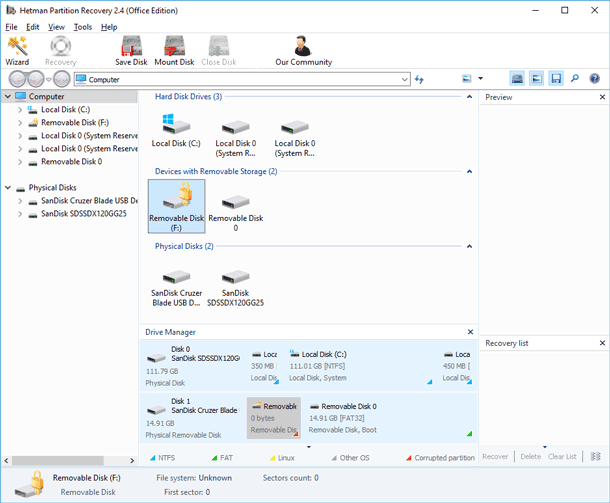
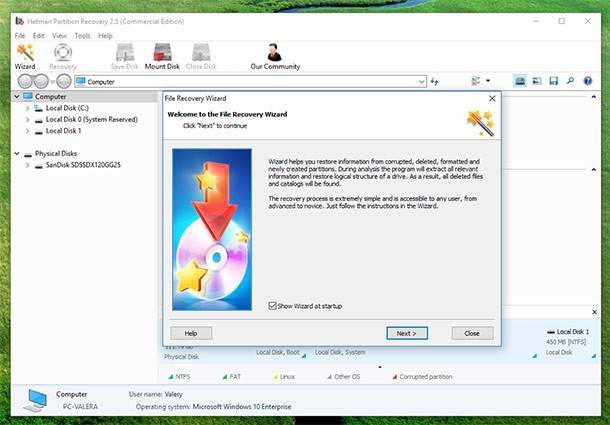
If your data could not be decrypted, and the problem with the encrypting virus was solved by cleaning the hard disk, we can still recommend using Hetman Partition Recovery to recover original versions of the lost files. After all, the encrypting software deletes them in a standard way after creating an encrypted copy, which means they can be recovered in a traditional way either.