Recover Files from TrueCrypt or VeraCrypt Disk: Expert Guide
Learn how to recover files from TrueCrypt or VeraCrypt encrypted disks with our essential guide. Whether you’ve forgotten the password, encountered disk errors, or need to access encrypted data for recovery purposes, it’s crucial to understand the process of decrypting and retrieving files from encrypted disks. In this comprehensive tutorial, we’ll walk you through step-by-step instructions and expert techniques to help you successfully recover files from TrueCrypt or VeraCrypt encrypted disks. From identifying the appropriate recovery methods to executing decryption processes, you’ll learn everything you need to know to ensure successful data retrieval. Don’t let encryption barriers hinder your data recovery—watch our guide and unlock your encrypted files today.

- What is TrueCrypt and VeraCrypt, and why would we use them?
- How to create an encrypted partition?
- How to mount and unlock the disk to access files?
- Recovering deleted files from a VeraCrypt container
- Questions and answers
- Comments
If you are looking for an easy and effective way to encrypt all computer data, from the system or logical disk and to a backup disk, external USB drive or a memory card, use VeraCrypt. This is an open-source tool meeting the highest data encryption standards.

How to Encrypt System Disk C with BitLocker in Windows 10 Without TPM, Enable TPM 🤔🔐💻
What is TrueCrypt and VeraCrypt, and why would we use them?
The best way to protect your files from being viewed by other people is to encrypt them. The encryption tool uses a secret key to turn the file contents into a mishmash of symbols. There is no way to read the contents until an unlocking key is used.
The VeraCrypt tool is based on the very popular open-source utility, TrueCrypt. After the TrueCrypt project was closed, a company named IDRIX added new features to the product and fixed security issues.
With VeraCrypt, you can create an encrypted container which can be then mounted in your system as an ordinary disk. All files from this container are encrypted and encrypted on-the-fly. That is why you can view and edit them just as if they were located on your USB drive. When you finish working with them, the tool blocks access to this container, and cleans the keys and file contents from the system memory.
VeraCrypt can also encrypt your system drive, but we recommend using the Windows-integrated tool, BitLocker. A peculiarity of VeraCrypt is the ability to create a hidden encrypted partition. If you are held by law breakers, and demanded to give the key, you can let them have a fake unlocking key that will open the fake volume you have created beforehand. Meanwhile, using the main key will unlock a different volume containing real data.
| Parameter | TrueCrypt | VeraCrypt |
|---|---|---|
| Purpose | Creation of encrypted file containers, partitions, and disks. | Creation of encrypted file containers, partitions, and disks with enhanced security. |
| Platforms | Windows, Linux, MacOS | Windows, Linux, MacOS |
| Encryption algorithms | AES, Serpent, Twofish, and their combinations. | AES, Serpent, Twofish, Camellia, Kuznyechik, and their combinations. |
| Boot encryption support | Yes | Yes (with improvements against brute-force attacks). |
| Performance | High, but less optimized for modern processors. | Optimized for modern processors, improved performance. |
| Current status | Development stopped in 2014, potential vulnerabilities exist. | Actively developed, vulnerabilities are patched, and features are added. |
| Advantages |
– Easy to use – Supports system disk encryption – Works on older systems |
– Stronger protection against attacks – Support for new algorithms – Compatibility with TrueCrypt containers |
| Disadvantages |
– Vulnerabilities due to lack of support – Limited protection against modern attacks |
– More complex setup process – Rare compatibility issues |

How to Encrypt a USB Disk with BitLocker, Unlocking with Password or Recovery Key 🔐💻⚕️
How to create an encrypted partition?
Download and install the program, then open the Start menu and run VeraCrypt. You will see the main window:
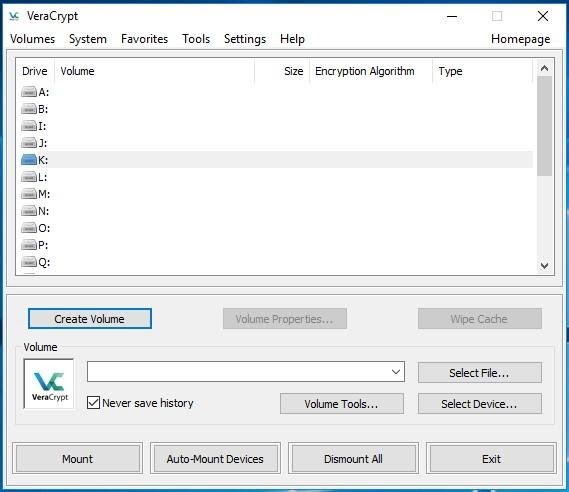
The first step to take is to click Create Volume. This starts the Volume Creation Wizard that offers you a choice of the following options:
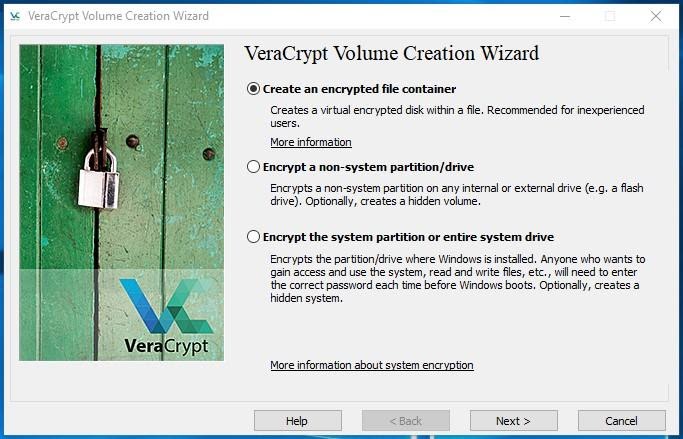
Creating an encrypted file container lets you generate such file on any disk currently connected to your computer. After that, such file can be mounted as a logical disk. Inside the file, a standard or hidden VeraCrypt volume can be created (we have just explained the difference above).
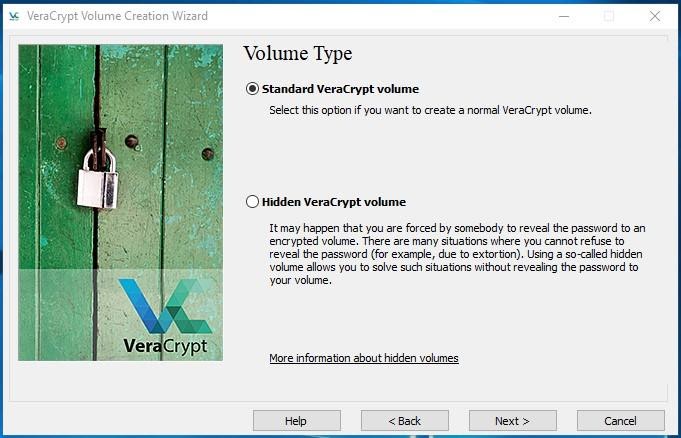
We will create a standard volume. The next step is choosing the volume location.
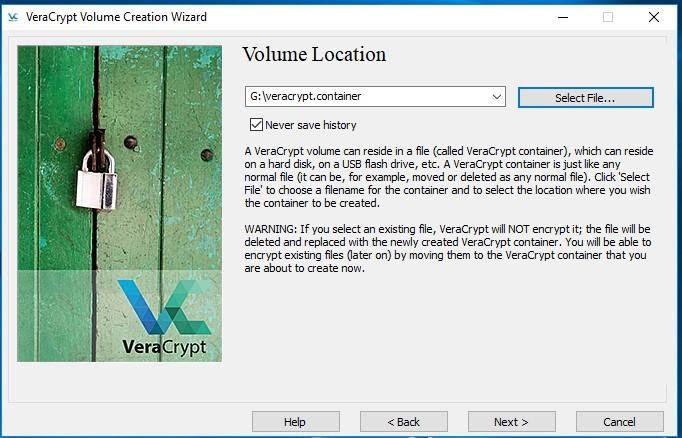
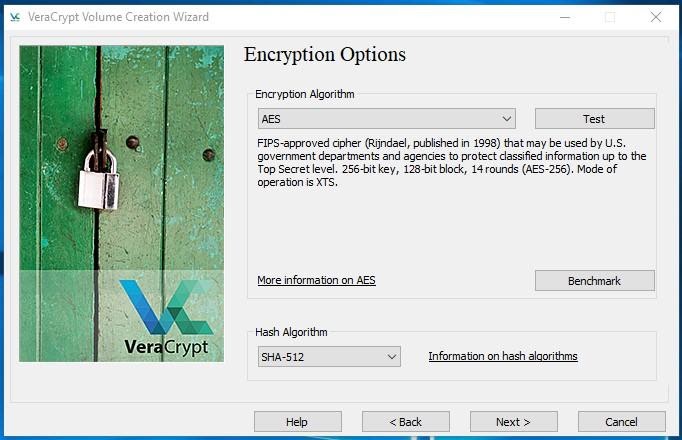
After that, decide on Encryption Algorithm and Hash Algorithm. By default, these are AES, and SHA-512, accordingly. Leave the settings as they are.
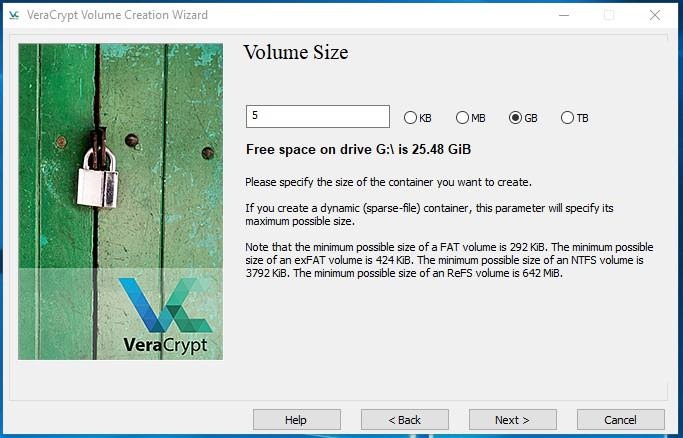
Now set the maximum volume size. Let’s set it to 5 GB.
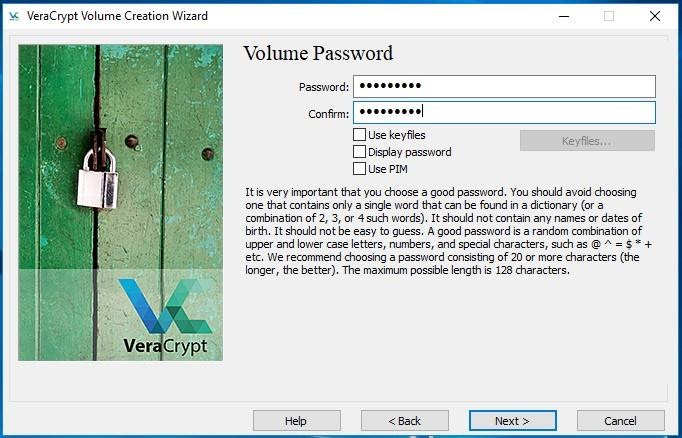
Click Next and go on to create a password. When the password is given, save it to a safe location or use a password which you remember well. There is no way to restore a forgotten or lost password, and you can’t decrypt the date without the password.
You can use any files that can be applied as an alternative to password, by checking the Use key files option.
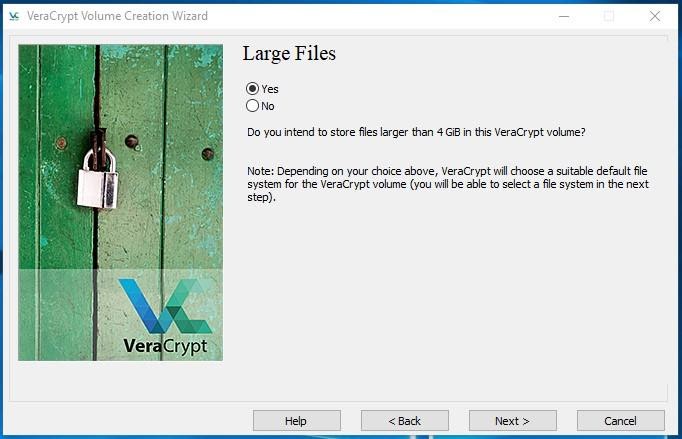
Click Next and confirm using large files.
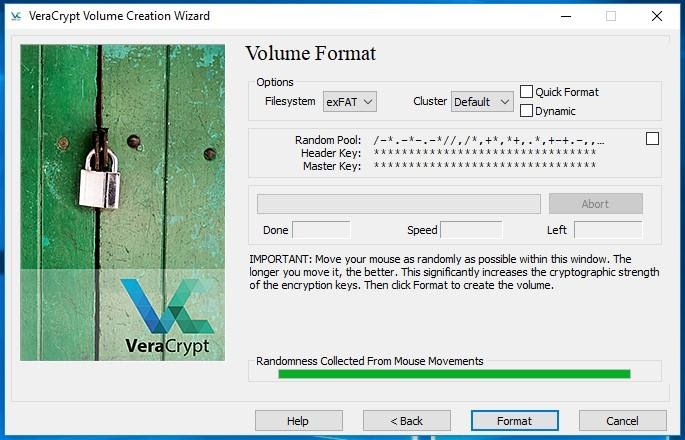
Click Next and move on to volume format options and encryption key settings. Click and wait until the encrypted volume is created.
How to mount and unlock the disk to access files?
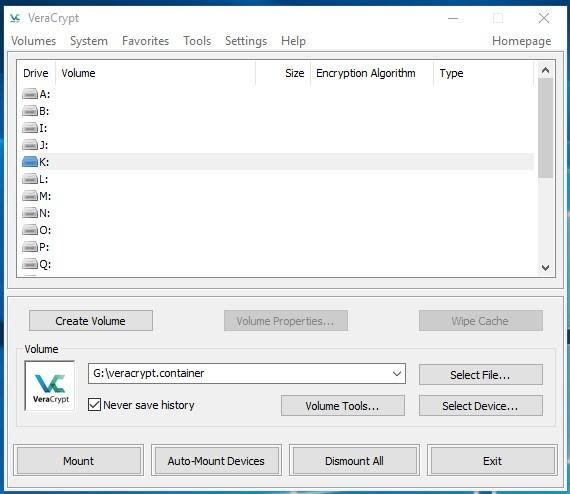
Click «Select File» in the program’s main window and choose the file where you saved the VeraCrypt container. After the file is chosen, select one of the available disks above. For example, let us select disk XXX and click on Mount.
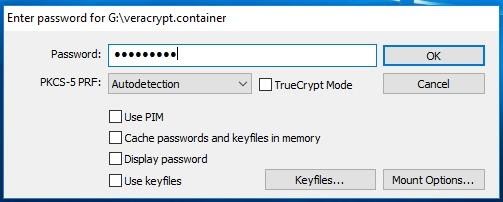
Now you need to enter the password.
Now go to This PC and check if a new disk appeared there.
Recovering deleted files from a VeraCrypt container
Files deleted by mistake or lost after formatting the encrypted disk can be recovered with the help of Hetman Partition Recovery. Before scanning, you should mount the disk in the program. As VeraCrypt uses on-the-fly encryption principle, the recovery process will be no different from working with any other disk.
Download and install it, then follow the wizard directions for effective file recovery.
Without the unlocking password, all data remains encrypted and can’t be restored.

How to Set a Password to File or Folder in Windows 10, 8 or 7 🔐📂💻