User Actions on Windows PC: Keeping an Eye on User Activities
Curious about how to view user actions on your Windows PC? In this article, we’ll guide you through step-by-step techniques for monitoring user activities on your Windows computer. From tracking browsing history to viewing file interactions, we’ll cover it all. Whether you’re a concerned parent or a vigilant employer, understanding user actions is essential for maintaining security and accountability.
In today’s article, you’ll see what information about user activity Windows can save, and how to view this data.
- Way 1. Browsing History
- Way 2. Search Engines
- Way 3. Recycle Bin
- Way 4. File Modification Date
- Way 5. Downloads
- Way 6. Sorting Programs by Date Modified
- Way 7. Windows Logs
- Way 8. Task Scheduler and Attaching Tasks to Events
- Questions and answers
- Comments

How to View Browsing History for Google Chrome, Mozilla Firefox, Opera, Edge, Internet Explorer 🌐⏳💻

How to View User’s Logins and Passwords Saved in a Browser for Facebook, Twitter, Instagram 🕵️🔍🔐
Way 1. Browsing History
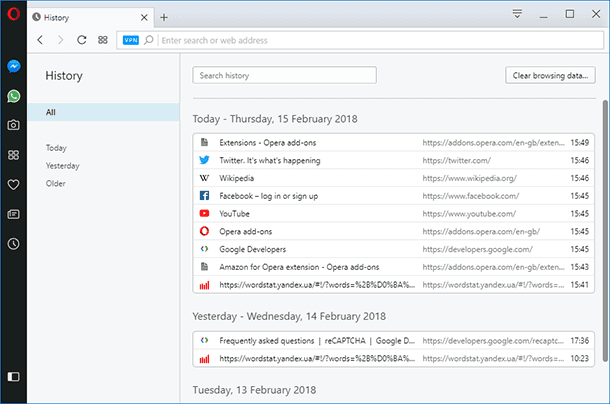
If you want to know if anyone used the computer and the Internet while you were away, the first and the easiest way to check it is to view browsing history.
There is a special article on this topic.
Way 2. Search Engines
To find a website, a webpage, a video or any other information on the Internet you need two things: an Internet browser and a search engine. Both tools can store browsing history, watch history (talking of YouTube), search history and search queries, and some tools can also save comments and posts in various online communities.
That is why the next way to view a user’s online activity is to check their activities in online accounts of various search engines.
Find a detailed article about it here.


How to Clear Browsing History and Cache in Chrome, Yandex, Opera, Firefox, Edge 📝🔥🌐
Way 3. Recycle Bin
Now let’s move from online activities to what users can do in Windows. We recommend checking the Recycle Bin as the first step. All the files deleted from this computer end up there.
To see if any files were deleted from the computer while you were away, open the Recycle Bin and select “Details” view option.
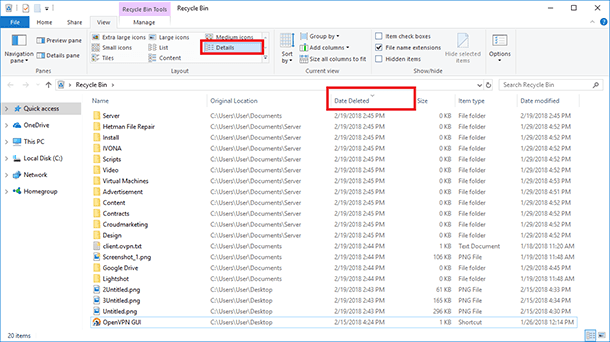
After that, sort the files by date of deleting, by clicking on the “Date deleted” heading. As a result, you can see files deleted recently.

How to Recover Files Deleted From Windows Recycle Bin or With Shift + Del 📁🔥⚕️
Way 4. File Modification Date
In Windows, you can sort files in every folder by the date when they were modified. Even if you don’t know where to look for files that could be modified without your knowing it, or while you were away, Windows has a good option for you.
Start the Run tool by right-clicking on the Start menu or pressing the shortcut Win + R.
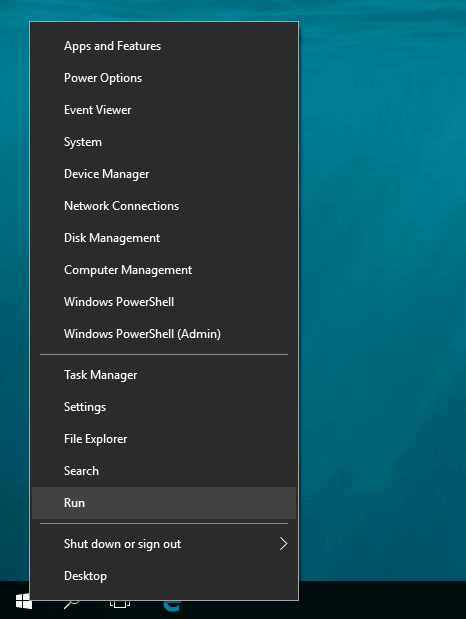
In the field “Run,” enter the command recent and click OK.
recent
A folder containing recently modified files will open, with the files being sorted chronologically, beginning with the latest changed files.
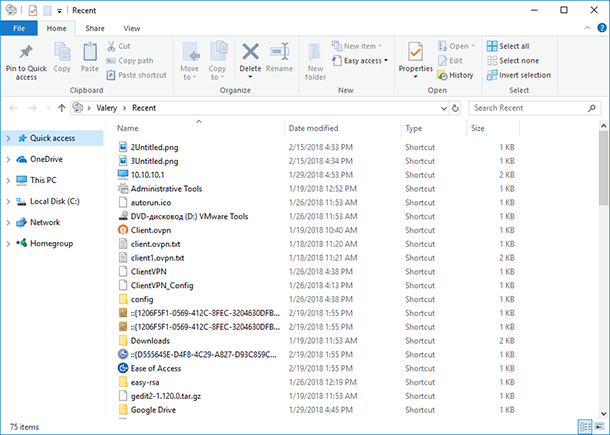
Way 5. Downloads
By default, all browsers save files from the Internet into the system folder “Downloads.” Go to this folder, and sort the files by download date, so you can see the latest files downloaded to this computer. There might be some stuff which you did not download, but someone else did...
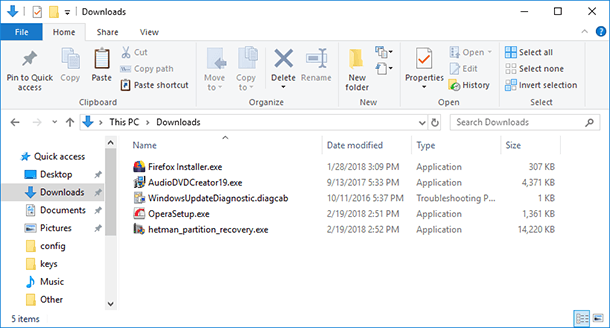
If the browser default folder for downloads has been changed, you should check it too.
Way 6. Sorting Programs by Date Modified
All programs on the computer are started with executable files having the “.exe” extension. To learn the date and time when a program was started:
-
Open the folder “This computer” and enter “.exe” in the search field. As a result, the search window will show you all files with this extension type on this computer.
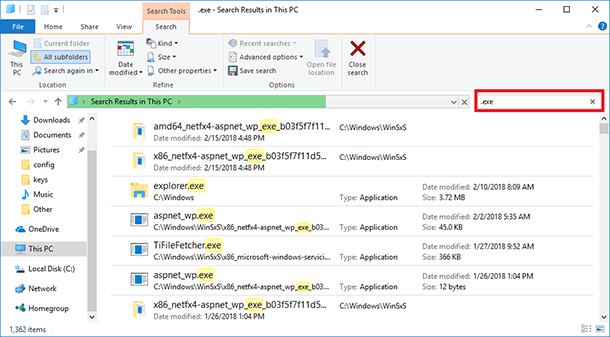
-
Right-click on the heading of any column, and select “Details”
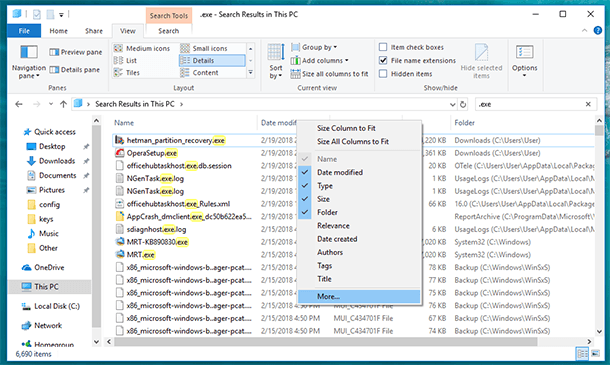
-
The window to choose columns will open. Find the line “Date modified”, check the box next to it and click OK.
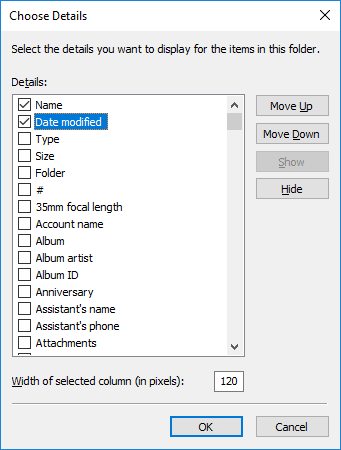
-
A new column called “Date modified” will appear in the search results window.
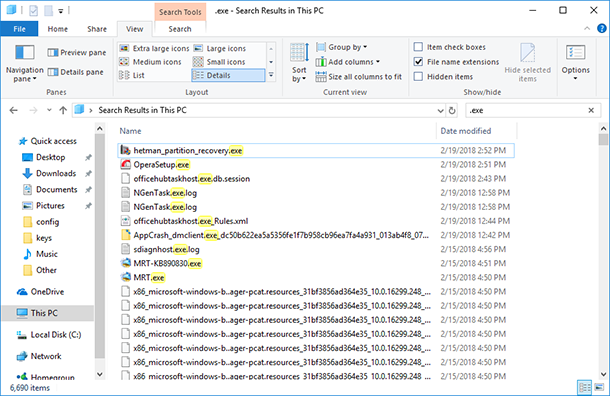
Now you can see the date when this or another program was started on this computer. If you don’t understand what program is hiding behind a particular .exe file, you can check it in Location column, or even start the program right from the search results window.
Way 7. Windows Logs
In Windows logs, the operating system records and saves all events, registers errors, information messages and warnings from applications, as well as the information on user activity and work of the operating system.

Windows Event Viewer: How to View Information about Errors in Windows 7, 8, 10 💥📜💻
To go to Windows Logs, open Control Panel / Administrative Tools / Computer Management.
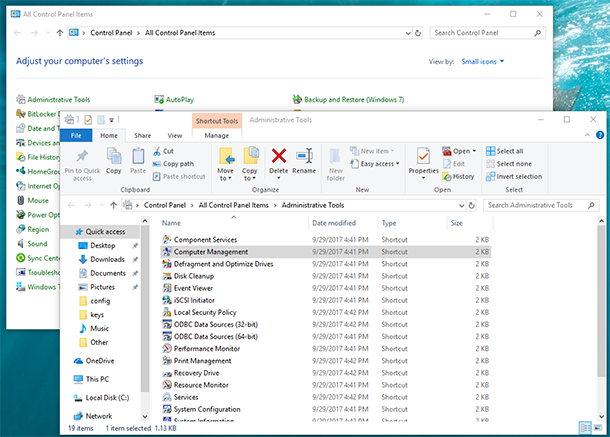
In Computer Management, go to System Tools / Event Viewer / Windows Logs.
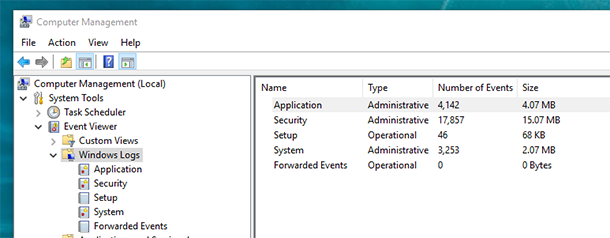
Logs are arranged by category. For example, application logs can be found in Application category, and system logs – in System category. If the computer has security events monitoring enabled, for example monitoring for logging in, then events are registered in the Security category.
Certainly, the information shown in Windows Logs are meant for system administrators, and ordinary users will have difficulty understanding it. Nevertheless, if you look at it more attentively, in the Application log you can see events generated by applications arranged in a sort of chronological order.
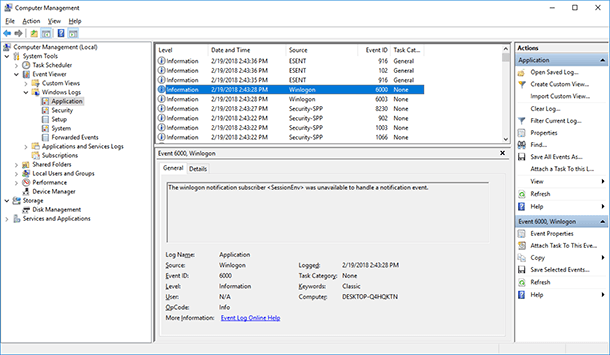
There is also some data on the date and time of logging in and off the operating system. In other words, it means the time when the computer was turned on or off. You can find this information in Security and System logs.
Way 8. Task Scheduler and Attaching Tasks to Events
Using Windows Logs, you can attach executing a task to a certain event in the log. For example, you can set up the computer to send a message to your email address every time your account logs on in Windows.
For example, I have an event in the Security log at logon. Its code is 4624. To attach a task to an event, right-click on the event and select “Attach task to this event.”
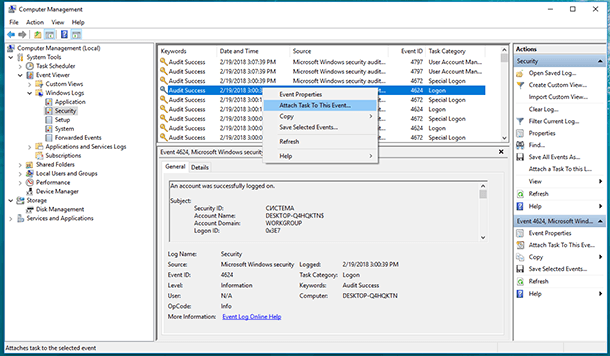
Then follow the steps in the Basic Task Wizard, and in the line “Action” select “Send an e-mail.”
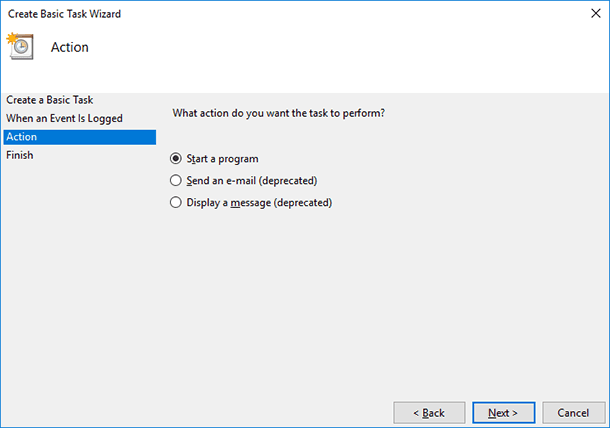
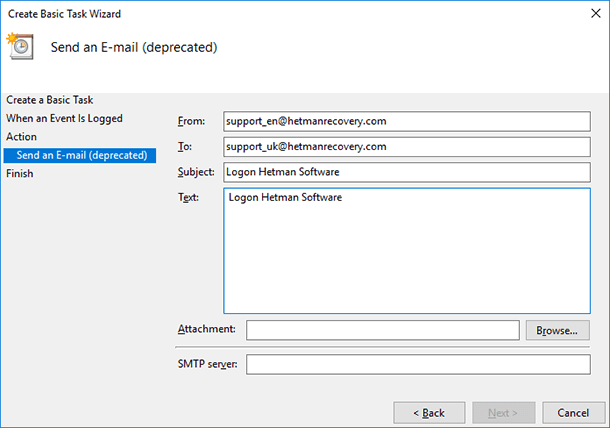
Enter the addresses where to send the message, the theme and text, and then the SMTP server for your mail service.
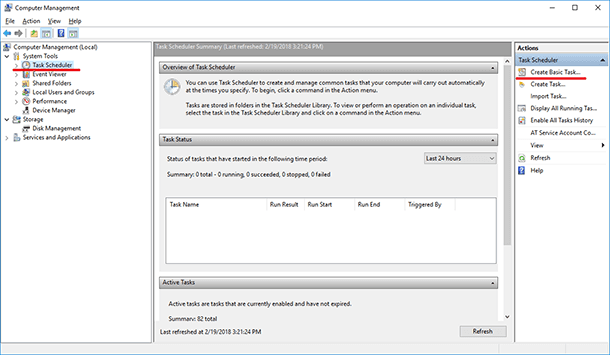
Similarly, you can create a task attached to an event by using Task Scheduler. To do it, go to Task Scheduler and select “Create Basic Task...”
Set up the task by using the same Basic Task Wizard.
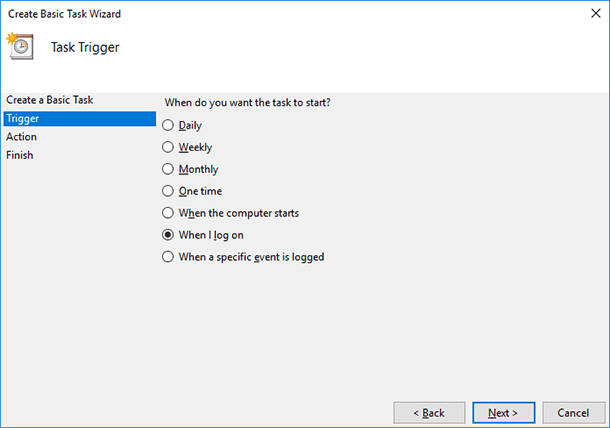
The picture shows how to set up the computer to send a message to your email address every time your account logs on in Windows, but in a similar way, you can set up the computer to perform other tasks attached to any event in the system log.